Disclaimer:
We are not affiliated at all with Fur Affinity staff, we just have an interest in cybersecurity and want to hopefully help stem the spread of misinformation by users.
Warning for slurs and other offensive language/imagery later in the post.
So, a brief timeline
This originally started on the 20th of August, 2024, at 4:51 UTC an announcement was put out stating
You may receive a 1016 error. We are working to resolve it. Thank you for your patience!
Error 1016 is a “Origin DNS error”, this will come up later.
Then at 4:59 UTC another announcement goes out
@FA Pings - Pinging so people read this channel. Dev is on it.
This is where everything kicks off at 5:59 UTC 2024-08-20, it started with the threat actor somehow gaining access to the registrar (We’ll discuss this later) and changing the domain so that it leads to a fake version of the FA homepage, likely to try and steal user info, however most people encountered an SSL cert error. The IT team confirms, “at no point in time, as far as I can tell, did FA domain resolve to an actual valid webpage which could have grabbed session data.”
Jansither (also known by luffy in the FA Discord) was quick to notify everyone of the attack and notify people in a (now deleted) tweet.
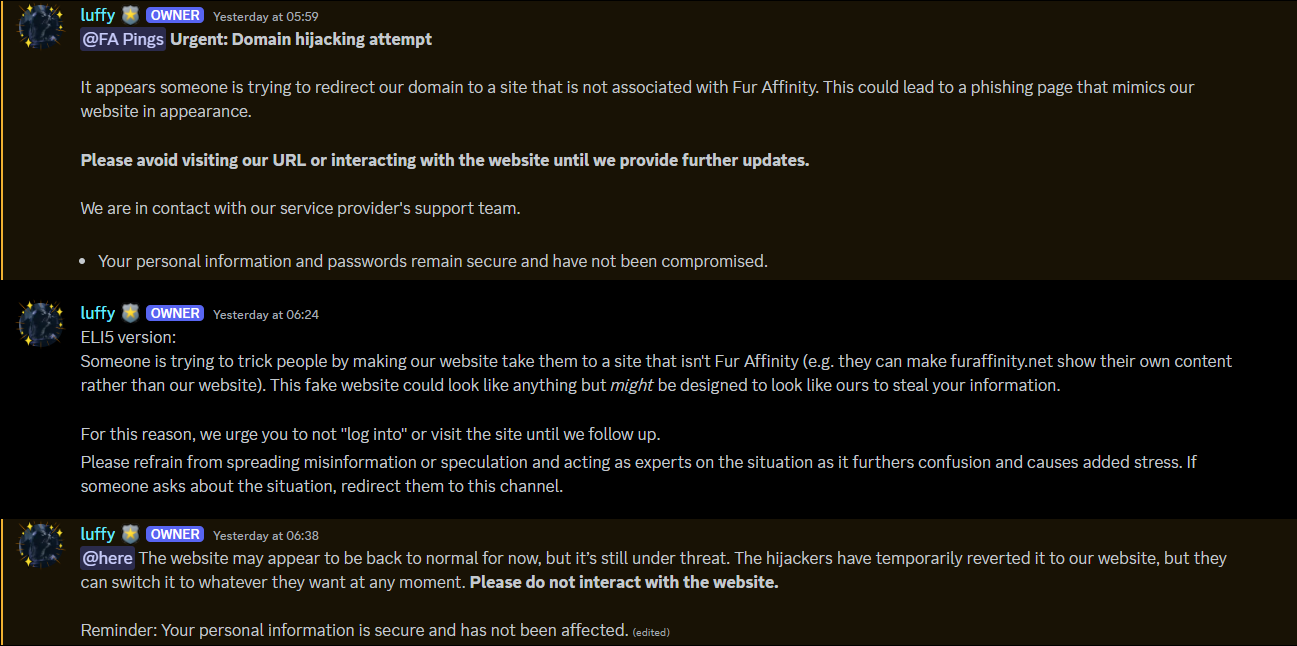
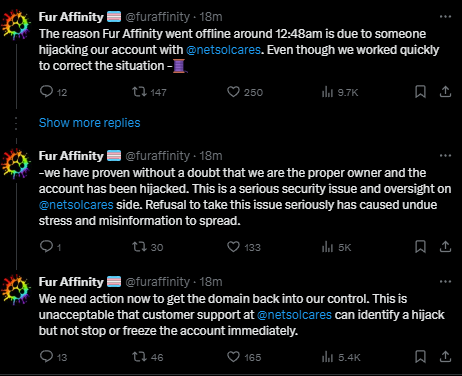
Unfortunately, NetSolCares’ (FA’s domain registrar) customer support claimed they cannot freeze or lock the account and that staff would have to wait 24-48 hours for proper assistance.
The reason Fur Affinity went offline around at 12:48am is due to someone hijacking our account with @netsolcares. Even though we worked quickly to correct the situation, their customer support has stated they cannot lock or freeze the account and we have to wait 24-48 hours for proper assistance. We have contacted them multiple times expressing urgency in this matter, and they’ve responded saying there is nothing they can do even though we have proven without a doubt that we are the proper owner and the account has been hijacked. This is a serious security issue and oversight on their side. Refusal to take this issue seriously has caused undue stress and misinformation to spread. We need action now to get the domain back into our control. This is unacceptable that customer support at @netsolcares can identify a hijack but not stop or freeze the account immediately.
The Fur Affinity staff were quick to invalidate all login sessions at 23:21 UTC 2024-08-20 and disable logins entirely at 23:42 UTC 2024-08-20
From here, everything starts to go down hill.
At an unknown time between 23:42 UTC 2024-08-20 and 00:18 UTC 2024-08-21 the Fur Affinity official Twitter account was accessed by threat actors, and proceeded to tweet out a deluge of tweets ranging from accusations of paedophilia against the late site owner Dragoneer, to insults and slurs and later endorsing Kiwi Farms
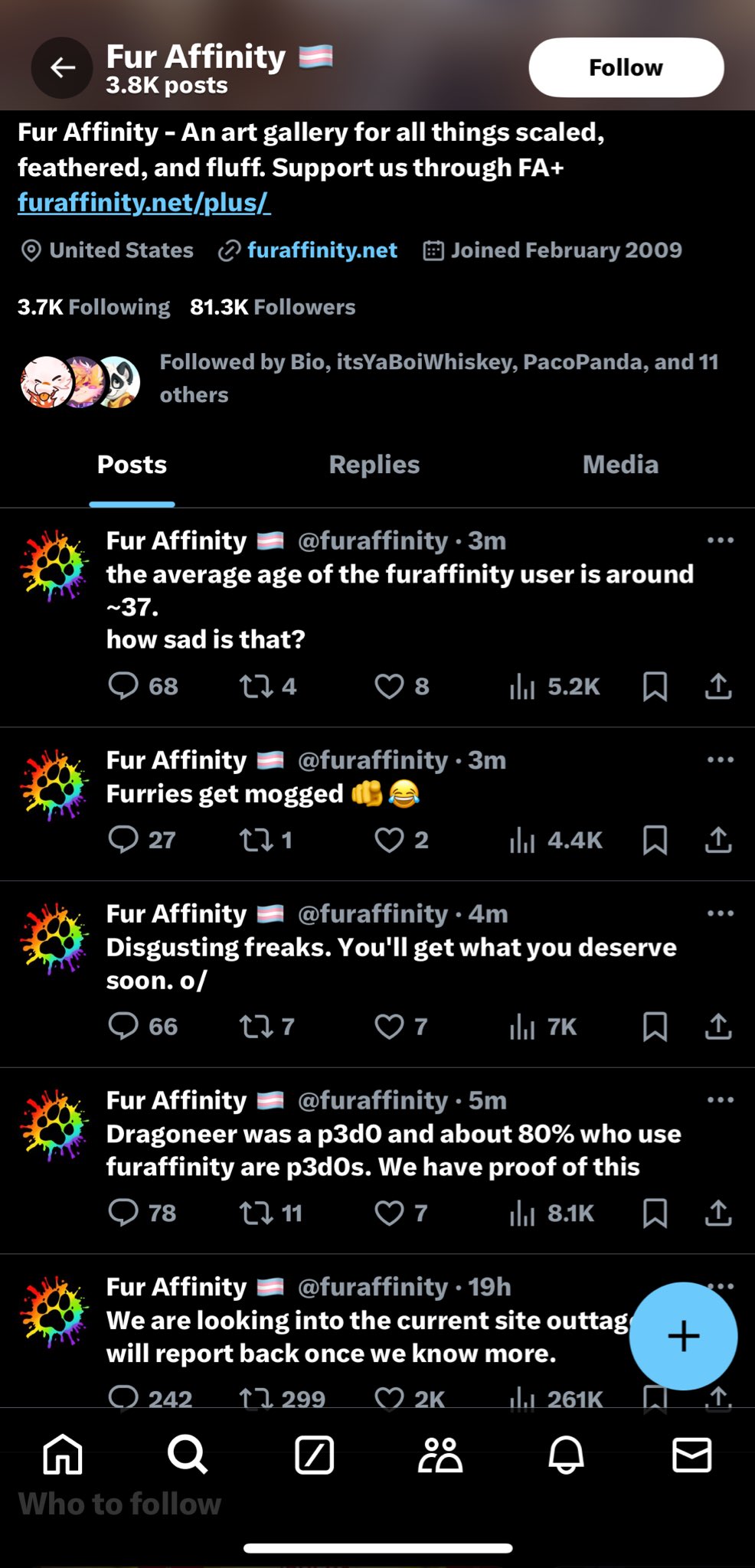
It then announced at 00:18 UTC 2024-08-21 that the Fur Affinity Twitter account has been compromised via the Discord.
@everyone The Fur Affinity Twitter has been compromised. We’re doing everything we can to regain access, but please do not trust anything posted on there until we let you know here that we have control of it again. Please tell those you know that they must rely on our Discord for information for now. Please report tweets made by our account
Around 00:31 UTC 2024-08-21, a tweet is made from the Fur Affinity twitter announcing:
A furry mascot is coming to Solana. Look out! ^.^
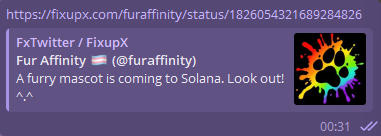
Then around 00:34 UTC 2024-08-21 a crypto mascot account is shared, which is quickly reported and suspended by Twitter
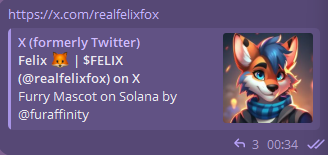
A pump.fun link is shared at 00:38 UTC 2024-08-21 using the same AI generated mascot as their image, it is also retweeted by Dragoneer’s compromised account.
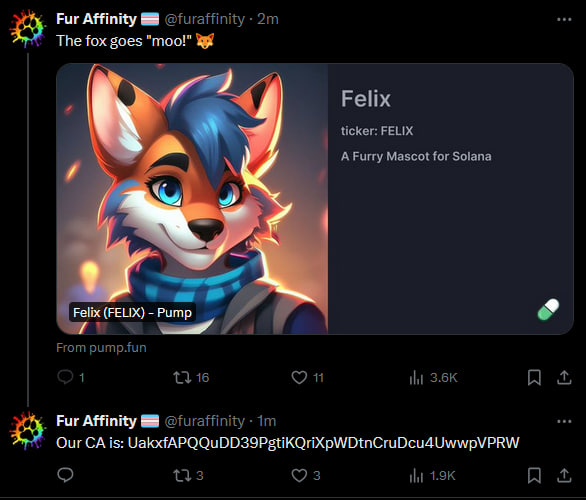
The wallet that created this token then minted 1,000,000,000 FELIX (≈ 4,243.19 USD) and transferred himself 60,735,849.056603 FELIX (≈ 1.8 SOL ≈ 255.86 USD)
He then transferred it to another wallet and transferred an additional 90,298,755.265211 FELIX (≈ 382.46 USD);
From there he sold all 151,034,604.322 FELIX for 5.8264 SOL (≈ 827.06 USD) meaning overall he only made $189 from his pump and dump scheme.
Around 1:42 UTC 2024-08-21, the official Fur Affinity Twitter’s handle is changed to @ilovekiwi4lunch and the @Furaffinity Twitter handle is sniped by a furry who goes by WHANOS who is currently holding it until the situation is resolved, at which point it will be transferred back to the Fur Affinity staff.
Some time between the retweets of crypto posts and 2:03 UTC 2024-08-21 the account of Dragoneer begins tweeting, including posts about and leaking his private messsages with some users (Will not be shown, now deleted).
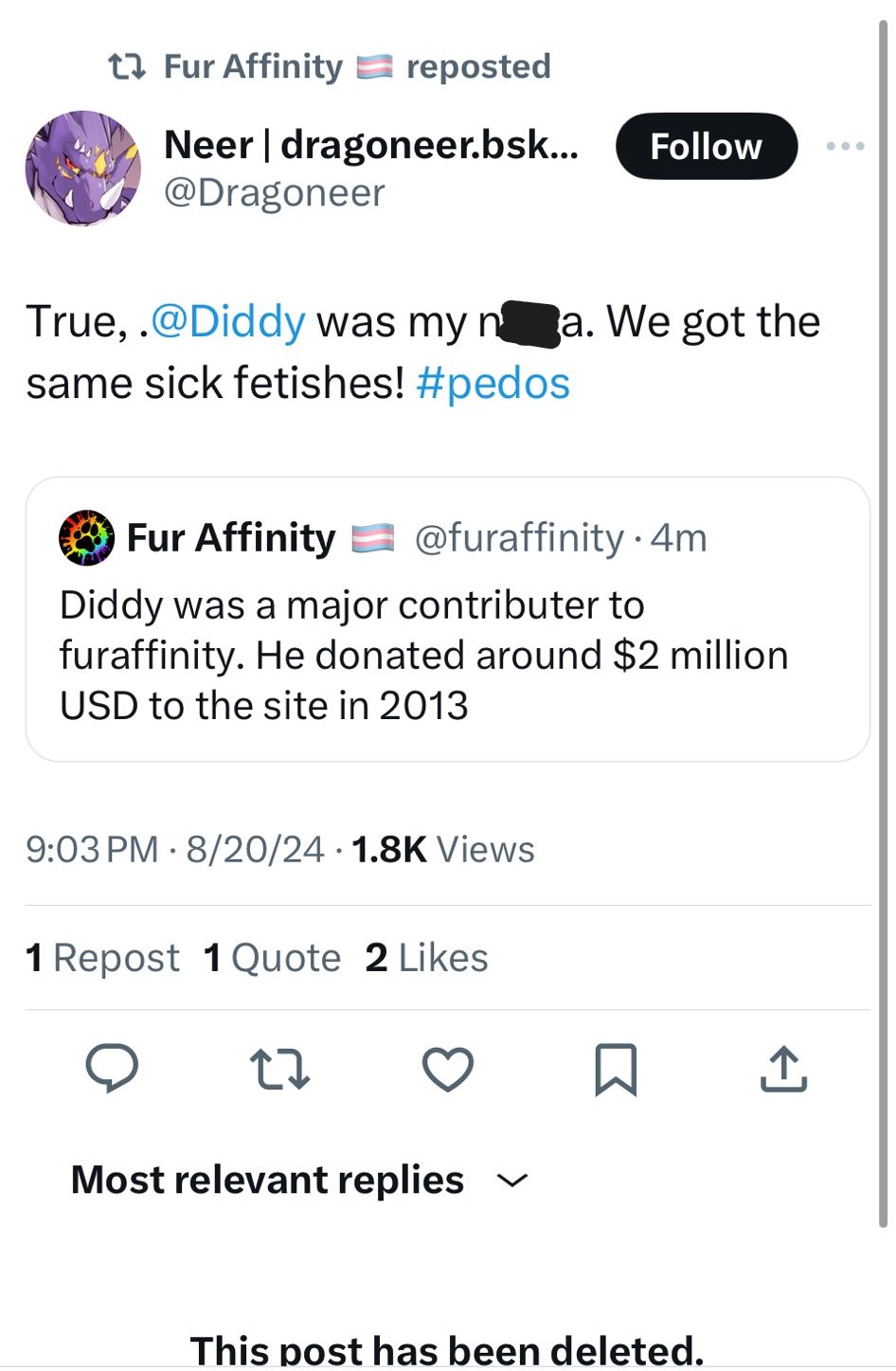
This all continues for around 40 minutes, at which point the Fur Affinity URL is pointed towards a Washington Post article.
Around an hour later, it is changed to point to Kiwi Farms who deny any wrongdoing in the situation.
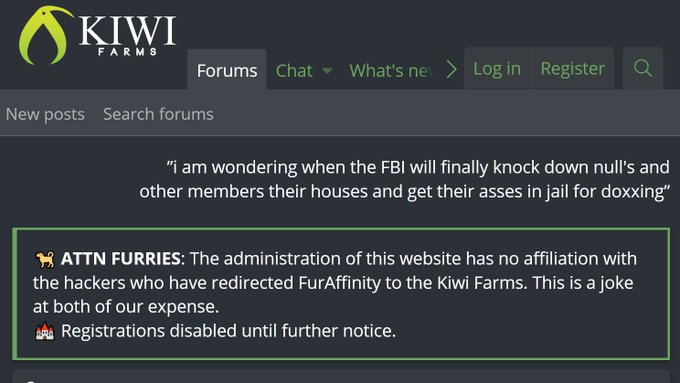
Since then the account has repeatedly tweeted and deleted nonsensical things, and has since gone silent. The hacking group known as NullBulge released tweets related to the situation.
Imagine hacking a website but doing it so poorly and unplanned that you got caught before even doing anything! @ilovekiwi4lunch is the definition of script kid. If you want real furry hackers maybe follow us instead, We actually hack and don’t get saved by companies being garbage
— NullBulge (@NullBulgeGroup) August 21, 2024
UPDATE AS OF 14:55 UTC 2024-08-21
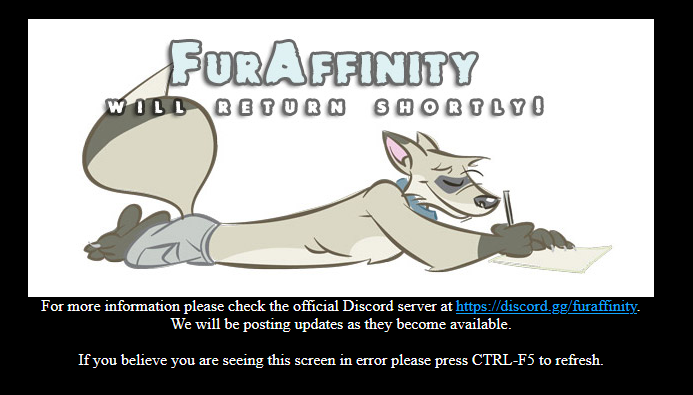
furaffinity.net has been successfully recovered by the Fur Affinity team, and is currently offline.
From Jansither:
Great news @everyone! We’ve connected with all necessary contacts and finally made progress in recovering our domain. The tech team has regained control and temporarily locked down the site while they double-check everything and continue to move things forward.
UPDATE AS OF 2:09 UTC 2024-08-22
The Fur Affinity Team has regained control of the main Twitter account. The website is still currently offline while security checks are undertaken, it will return soon.
What exactly happened?
This is where the facts end and (educated) speculation mostly begins.
What we do know:
- Threat actors had access to the Network Solutions account that hosted the Fur Affinity domain
- They used this access to change the DNS Records of the domain, most notably the DNS NS (Nameservers)
Using this knowledge, it’s a fair assumption to make that the DNS MX records were changed too, most likely using a wildcard email address to redirect any and all mail traffic going to @furaffinity.net emails to their own inboxes; this includes password reset requests for the accounts @Dragoneer and @FurAffinity, the threat actor confirmed that Dragoneer had an email of dragoneer@furaffinity.net (To my knowledge, the Fur Affinity team use Google Suite for their email provider.)
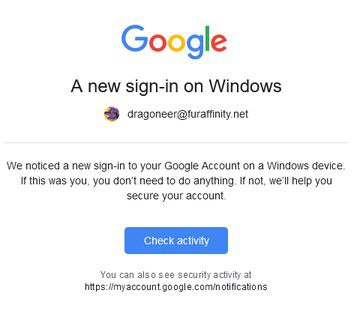
How did they get into the registrar account in the first place?
Unfortunately we don’t know currently, and likely won’t be told any time soon, but our best guess would be a reused password from another website that got leaked online. This is why you should ALWAYS USE DIFFERENT PASSWORDS, and ideally store them in an offline password manager (Personally we highly recommend Keepass).
In Conclusion
Currently, this is about everything we know. We’ll keep it updated in case things happen later on. If anything in this timeline is incorrect please feel free to notify us via social media channels or our email nebula@neb.gay and we’ll be happy to change it.
Please try and stay safe on the internet folks, this could’ve been mitigated by better security on the end of the registrar, now all we can do is hope they do something sooner than later to avoid any more damage being done.
See you Space Cowboy :3
~ Nebula System
>> Home